Planning your Cyber Strategy for 2021? Here’s What You Need to Know:
by Security Centric, on 02/02/2021 10:36:23 AM
As most companies come fully back into the office from the holiday period and Australia adjusts into a “COVID normal” routine, many organisations are in a place to plan strategy for the coming year with a higher level of certainty than they could in 2020. This includes looking at their cyber security budget and strategy for the coming year.
Which begs the question - with so much to do in the realm of cyber security, what’s important to consider when making recommendations to the board about actions to take, or allocating additional budgets? While the answer will generally be unique to each organisation, looking at what the data tells us about the current threat landscape can help to structure a strategy.
3rd Party Risk and Supply Chain: aka the SolarWinds Fallout:
Although there haven’t been any major data-based reports released around the fallout from the SolarWinds breach yet, what we’re seeing and hearing from clients is that there is already an increase in the amount of assurances being requested by government and other 3rd parties as to the security of their systems. What organisations are likely to experience is an increased need to show any potential clients that security is a focus, whether this be in the form of a risk register, compliance framework adherence, or regular assessments and testing.
Additional Reading: You Think You’re Prepared for the Next SolarWinds. You Are Not.
Recommended Services: Cyber Security Maturity Assessment, Compliance Certifications, Managed Security Services.
Adjunct Services: Penetration Testing, Security Engineering Services (for hardening and implementation)
Vulnerabilities, Malware, and Threat Detection:
There have been multiple reports released by the likes of Tenable, Datto, Verizon, Seqrite, and Microsoft around the number of vulnerabilities, malware, ransomware threats, and data breaches throughout 2020. Throughout these, the message is clear: the rapid change in digital environments due to COVID and work from home environments has increased attack surfaces and opportunities for payoffs, and we’ve seen some of the largest numbers of cyber threats and CVEs to date.
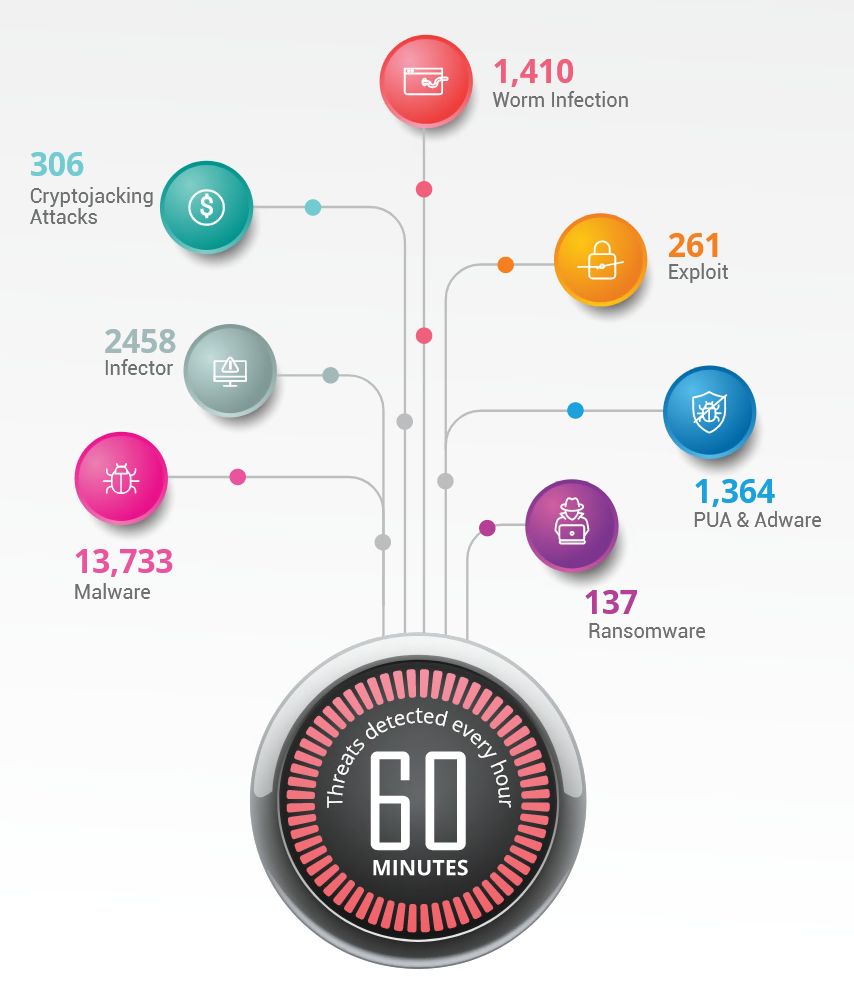
The diagram below outlines the number and types of threats per hour against a Windows based system, and it paints a picture around the importance of proper vulnerability and threat detection. Making sure you have a threat monitoring and detection system in place, along with an understanding of what your organisation’s baseline or “normal” looks like are necessary in order to respond as quickly as possible to any threats that are outside of what you’d normally expect to be seeing.
The ability to respond quickly and efficiently to a threat will save your organisation time and money, and should be a part of your breach prevention strategy.
Additional Reading:
Tenable 2020 Threat Landscape Report
Seqrite Annual Threat Report
Verizon DBIR
Recommended Service/s: Managed Security Services (Encompasses Vulnerability Scanning, Threat Detection, and SIEM services, or block hours for Incident Response and Testing/Assessments), Vulnerability Scanning, Penetration Testing.
Ransomware:
Ransomware saw a massive increase during 2020, and since the work from home situation is becoming part of the COVID normal for Australia, and certainly is still a large part of life for those in other parts of the world, we can expect that it’s going to continue to be a risk throughout 2021. A big factor in this is how profitable it is for threat actors. This, alongside the increase in cyber insurance which is often used to cover ransom payments, means that it should be high on your list of priorities to protect against.
There’s no one-fix for ransomware. The usual ingress for these types of attacks are through phishing. A recent report from Datto indicates that 50% of ransomware in 2020 got through anti-virus/anti-malware solutions. Protection against ransomware requires a number of controls to be in place, and the end goal needs to be resilience against ransomware in addition to having a response plan for the “not if, but when” scenario of your business experiencing an attack.
Additional Reading:
Datto's Global State of the Channel Ransomware Report
Ransomware 2020: Costs, Risks, and Realities
Recommended Service/s: Ransomware Protection
Adjunct Services: Simulated Phishing, Security Awareness Training, Office 365 Assessment.
Business Email Compromise:
Again the remote work situations that many organisations find themselves in has increased the risk for Business Email Compromise. Being on top of your cloud security, your O365 controls, authentication and access controls, as well as as monitoring and alerting being in place can help to respond and recovery rapidly to any email breaches.
Recommended Service/s:
Office 365 Assessment, Cloud Security Assessment.
Adjunct Services: Security Engineering Services (Hardening and Implementation), Simulated Phishing, Security Awareness Training.
Phishing:
Phishing is, and will continue to be a key point of attack for threat actors looking to achieve a breach. An employee clicking on a dodgy link can result in a ransomware attack, malware being downloaded for an advanced persistent threat, or business email compromise. A robust cybersecurity strategy should include regular security awareness training for staff who don’t have security knowledge, and simulated phishing campaigns to foster practical awareness as well as a culture of “if you click it, just admit it”. The faster an employee makes security teams aware of a possible phish, the better.
Additional Reading: Terranova + Microsoft Gone Phishing Tournament
Recommended Service/s:
Phishing Simulation, Security Awareness Training
Need more information on how you can structure your cybersecurity strategy for the year or want to know more about any of the services mentioned? Contact Us to speak to a business security advisor.
.png?width=400&height=53&name=logo%20(1).png)

.png?width=423&height=56&name=logo%20(1).png)