The best threat detection solution considers what is happening with where it is happening, combining organisational context with threat intelligence and event correlation. Working with a security specialist to understand the best fit for your specific needs can help make the process of setting up and managing threat detection more effective with less cost.
Security Information and Event Management (SIEM) is a complex solution, involving design, deployment, development and management phases. At Security Centric, we provide management and assistance throughout the SIEM lifecycle. We can help you choose the right threat detection/SIEM solution, ensure your policies and procedures maximise their value and enable you to respond quickly and efficiently to relevant events and incidents.
The threat detection solution proposed is focused on providing actionable alerts 24x7 for high-confidence threats or suspicious behaviour, rather than a log aggregator producing numerous false positives.
Using a combination of machine data analytics and our information security consulting and engineering expertise, we’re able to analyse and correlate relevant sets of data to derive useful and actionable insights into notable security events. Stakeholders and end-users can be notified of specific security events via their preferred method of communication (e.g. Email, SMS, Teams, Slack etc). Relevant reports are also generated and made available on a periodic basis, which can be customised on request to suit any specific requirements. Event data is stored online and readily accessible for 12 months.
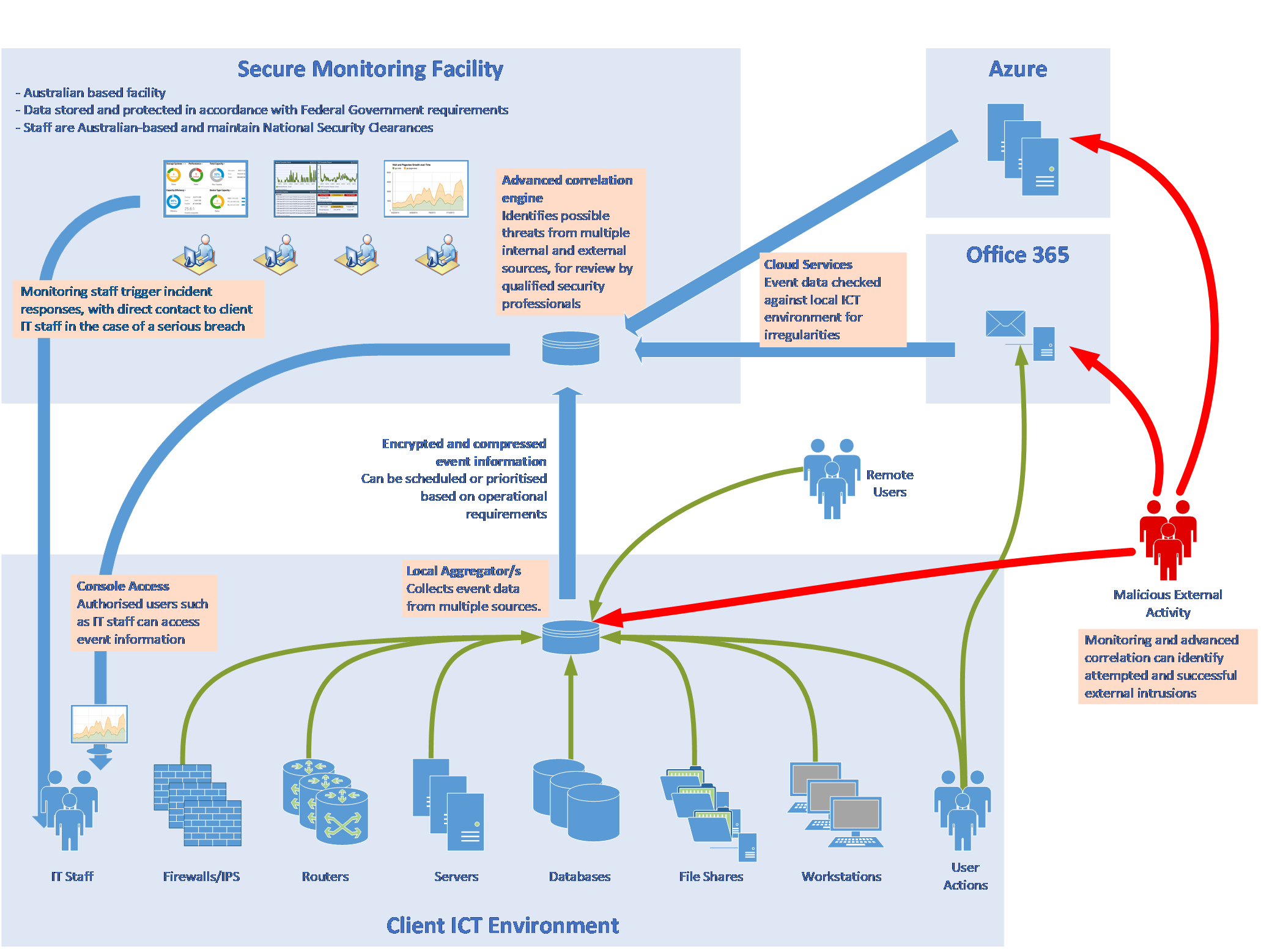
The threat detection solution is built on a cloud native platform that aggregates and ingests log data from critical pieces of infrastructure, which uses machine data analytics and automated threat intelligence to provide contextualised security information and event management. The solution combines many of the leading and effective approaches into a single integrated highly accurate threat detection platform. This is achieved through:
Contact us today to discuss how your organisation can benefit from advanced threat detection.
Level 34, 201 Elizabeth St
Sydney, NSW 2000
Call us: +61 2 9199 0000